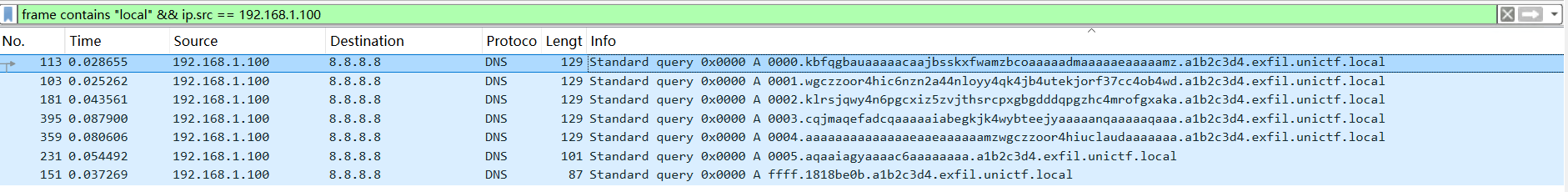
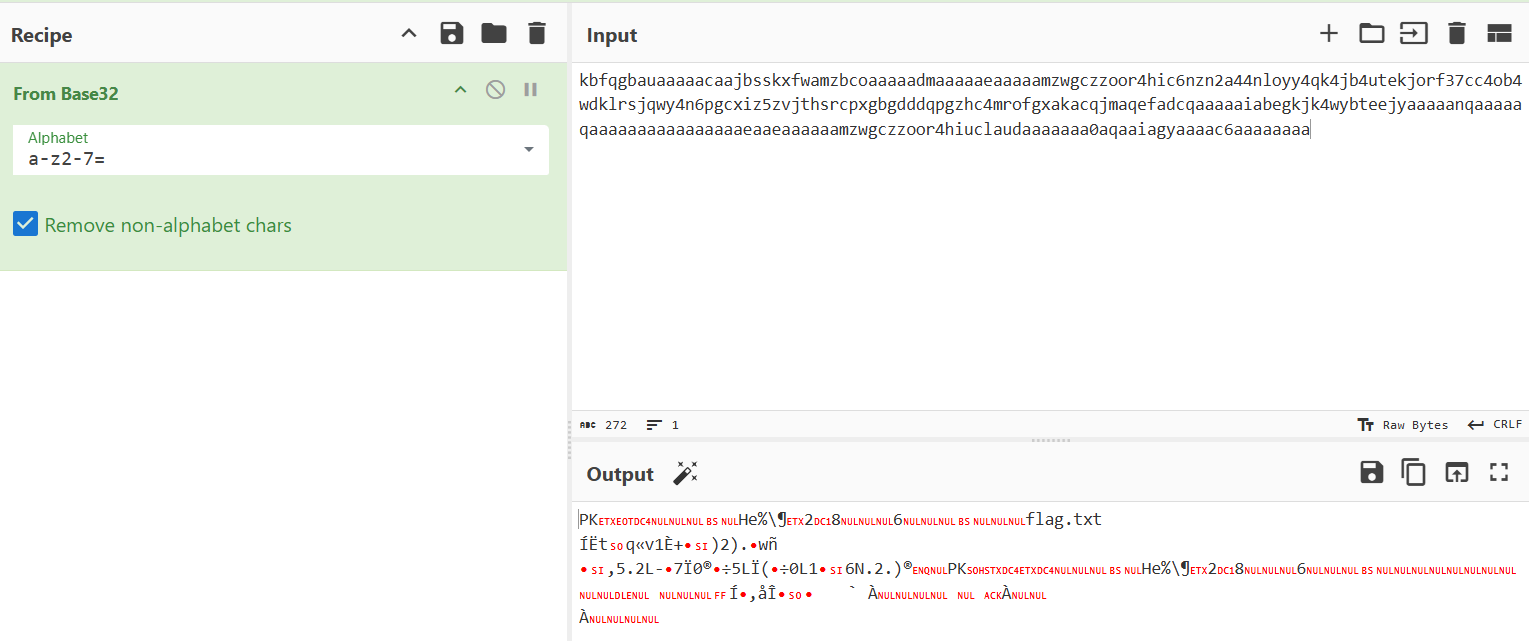
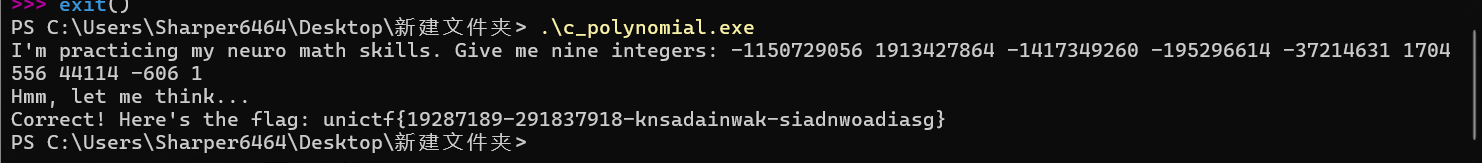
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
| from hashlib import sha256
from struct import unpack
import logging
import z3
logging.basicConfig(level=logging.DEBUG, format='[%(levelname)s] %(message)s')
xor_key = sha256(b'UnicornVM_Secret_Key_2026_CTF!!!').digest()
decrypt = lambda enc:bytes(xor_key[i&0x1F]^((i*7)&0xFF)^enc[i] for i in range(len(enc)))
opcode = [0xB, 0x17, 0x1C, 0x88, 0xBF, 0xD2, 0xBB, 0x80, 0xC5, 0x3D, 0x6F, 0x32, 0xBB, 0xD1, 0x6D, 0x63, 0x58, 0xD4, 0x9C, 0xBA, 0x57, 0x38, 0xC7, 0xE4, 0x9E, 0x27, 0xAE, 0x8C, 0xFA, 0x16, 0xF0, 0x4F, 0xFF, 0xF7, 0xF, 0xB1, 0xE2, 0x6D, 0x5D, 0x4C, 0x2F, 0xC5, 0xE2, 0xED, 0x76, 0x6F, 0x46, 0x42, 0x7A, 0xF1, 0xBD, 0x58, 0xB7, 0xD8, 0x27, 0xC4, 0xBB, 0x3, 0x8F, 0xAE, 0x98, 0x73, 0x92, 0x29, 0xDE, 0xD2, 0x2A, 0x93, 0xC0, 0x8B, 0x5, 0x15, 0x31, 0xED, 0x2E, 0x71, 0xFA, 0x90, 0x2C, 0x20, 0x1B, 0x95, 0xDC, 0x7A, 0x97, 0xF8, 0x7, 0x24, 0x5B, 0xE6, 0x6B, 0x4F, 0xBF, 0x52, 0xB0, 0x8, 0xAE, 0xA1, 0x4F, 0xF5, 0xA4, 0xA9, 0x26, 0x88, 0xAB, 0x31, 0x7, 0x7C, 0xA5, 0xDC, 0xD2, 0xB, 0x3A, 0xB7, 0xF9, 0x1B, 0xF5, 0x99, 0x67, 0x4, 0x7B, 0xC3, 0x4F, 0x6E, 0x5D, 0xB0, 0x55, 0xEA, 0x88, 0x80, 0x6A, 0xD0, 0x86, 0xCB, 0x40, 0x50, 0x73, 0xAE, 0xEF, 0xB3, 0x3A, 0x53, 0xED, 0xE1, 0xD9, 0x54, 0x1C, 0x3A, 0xD7, 0xB8, 0x42, 0x60, 0x1A, 0xA1, 0x28, 0xD, 0x7E, 0x91, 0x66, 0xC8, 0x69, 0x73, 0x8D, 0x33, 0xDD, 0x52, 0x9D, 0xBC, 0xBE, 0x31, 0x20, 0xD, 0x51, 0x32, 0xCF, 0xC4, 0xF8, 0x76, 0x3E, 0xDA, 0x37, 0x58, 0xA7, 0x44, 0x3B, 0x83, 0xA, 0x28, 0x1C, 0xF7, 0x7, 0xAD, 0x4C, 0x51, 0xAF, 0x15, 0x45, 0xA, 0x82, 0x95, 0xB1, 0x6E, 0xAF, 0xF2, 0x7B, 0x11, 0xAC, 0xA1, 0x99, 0x14, 0x5C, 0xFF, 0x13, 0x79, 0x85, 0xA3, 0xD8, 0x60, 0xEB, 0xDB, 0x3E, 0xD6, 0x34, 0x8A, 0x2F, 0x8A, 0x76, 0x88, 0xE9, 0xC7, 0x1D, 0x1B, 0x4F, 0x45, 0x4E, 0x10, 0x9E, 0xF0, 0x8E, 0x82, 0xB9, 0x34, 0x7C, 0x9A, 0x77, 0x18, 0xE7, 0x81, 0xFD, 0x42, 0xCD, 0xFA, 0xDB, 0x33, 0xD6, 0x68, 0x9, 0x12, 0xEE, 0x57, 0x7, 0x48, 0xC2, 0xD4, 0xF0, 0x2F, 0x6D, 0x33, 0xBB, 0xD1, 0x6C, 0x61, 0x5C, 0xD0, 0x9D, 0xB8, 0x50, 0x3B, 0xC4, 0xE0, 0x8E, 0x20, 0xAC, 0x89, 0xFC, 0x10, 0x4D, 0xF1, 0x14, 0x3E, 0xE3, 0x8, 0x4E, 0xB6, 0xE9, 0xF5, 0xD2, 0xA, 0xC, 0x51, 0xDF, 0xB1, 0x4C, 0x41, 0x79, 0xF4, 0xBC, 0x5A, 0xB2, 0xDE, 0x26, 0xC6, 0xAF, 0x5, 0x89, 0xAB, 0x9E, 0x76, 0x95, 0x28, 0xCB, 0xD6, 0x2F, 0x94, 0xC2, 0x8D, 0x3, 0x17, 0x33, 0xEE, 0x2D, 0x73, 0xFB, 0x91, 0x2C, 0x21, 0x19, 0x91, 0xD8, 0x7B, 0x95, 0xFF, 0x4, 0x27, 0x5F, 0xF6, 0x6C, 0x4D, 0xBA, 0x54, 0xB6, 0xB5, 0x10, 0x4A, 0x86, 0x19, 0x1D, 0x5, 0xFD, 0x3C, 0x12, 0xCC, 0xC8, 0x92, 0x19, 0x74, 0xC, 0x1, 0x39, 0xB4, 0xFC, 0x1A, 0xF7, 0x9D, 0x61, 0x5, 0x79, 0xD7, 0x49, 0x68, 0x58, 0xB6, 0x50, 0xED, 0x88, 0x95, 0x6A, 0xD6, 0x82, 0xCA, 0x42, 0x56, 0x71, 0xAF, 0xED, 0xB3, 0x3B, 0x51, 0xE9, 0xE5, 0xD8, 0x56, 0x1B, 0x39, 0xD4, 0xBC, 0x52, 0x67, 0x18, 0xA4, 0x2E, 0xB, 0xC3, 0x2F, 0x8D, 0x1, 0x85, 0xCA, 0x21, 0xE8, 0x69, 0xEB, 0x60, 0x73, 0x50, 0x8D, 0x8B, 0xD3, 0x5B, 0x31, 0xCC, 0xC1, 0xF9, 0x74, 0x39, 0xDC, 0x36, 0x5A, 0xB3, 0x42, 0x3D, 0x86, 0xC, 0x2D, 0x1B, 0xF7, 0x12, 0xAC, 0x4A, 0x55, 0xAE, 0x17, 0x43, 0x8, 0x83, 0x96, 0xB1, 0x6F, 0xAD, 0xF6, 0x7F, 0x10, 0xAE, 0xA6, 0x9A, 0x17, 0x58, 0xEF, 0x14, 0x7B, 0x80, 0xA5, 0xDE, 0xDD, 0x55, 0x30, 0xF7, 0x3A, 0x8D, 0x26, 0xF4, 0x3E, 0xCF, 0x75, 0x26, 0x29, 0xA1, 0xB1, 0x91, 0x4F, 0x4D, 0x13, 0x9B, 0xF1, 0x8C, 0x84, 0xBF, 0x35, 0x7E, 0x8E, 0x71, 0x1E, 0xE2, 0x87, 0xF8, 0x45, 0xCD, 0xEF, 0xD5, 0x35, 0xD2, 0x69, 0xB, 0x14, 0xEC, 0x56, 0x3, 0x48, 0xC3, 0xD6, 0xF4, 0x2B, 0x6C, 0x31, 0xBC, 0xD2, 0x6F, 0x65, 0x4C, 0xD7, 0x9F, 0xBD, 0x56, 0x3D, 0x79, 0x5E, 0x65, 0xE9, 0x40, 0x30, 0x50, 0xCB, 0xF9, 0x48, 0xE9, 0xF1, 0xD, 0xB4, 0xEB, 0x68, 0xE3, 0xF6, 0xD1, 0xF, 0xD, 0x53, 0xDE, 0xB7, 0x4D, 0x43, 0x6D, 0xF2, 0xBA, 0x5F, 0xB4, 0xDB, 0x21, 0xC7, 0xB9, 0x1, 0x8C, 0xAC, 0x9C, 0x7C, 0x93, 0x2A, 0xC8, 0xD5, 0x2C, 0x96, 0xC3, 0x88, 0x3, 0x16, 0x31, 0xEA, 0x29, 0x72, 0xF9, 0x96, 0x2F, 0x22, 0x1D, 0x81, 0xDF, 0x79, 0x90, 0xF9, 0x2, 0x9A, 0xE1, 0x1D, 0xA5, 0xA1, 0x3, 0xF8, 0x6D, 0x1, 0xA9, 0xB7, 0x49, 0xF7, 0xA1, 0xA1, 0x23, 0x36, 0x11, 0xCF, 0xCD, 0x93, 0x1B, 0x74, 0xA, 0x0, 0x3B, 0xA0, 0xFA, 0x1C, 0xF2, 0x9B, 0x64, 0x2, 0x79, 0xC2, 0x45, 0x6E, 0x5C, 0xB7, 0x52, 0xEB, 0x8A, 0x94, 0x6C, 0xD6, 0x83, 0xC8, 0x46, 0x52, 0x70, 0xAD, 0xEA, 0xB0, 0x38, 0x55, 0xF9, 0xE2, 0xDA, 0x53, 0x1D, 0x3F, 0x69, 0x2, 0xB9, 0xAE, 0xF4, 0x1D, 0x82, 0xD0, 0x77, 0x96, 0x70, 0xCE, 0x6B, 0x76, 0x86, 0x36, 0x63, 0xE8, 0x63, 0x76, 0x51, 0x8F, 0x88, 0xD5, 0x5A, 0x33, 0xD8, 0xC7, 0xFF, 0x71, 0x3F, 0xD9, 0x31, 0x5A, 0xA6, 0x4F, 0x3B, 0x82, 0xD, 0x2F, 0x1D, 0xF5, 0x13, 0xAB, 0x4A, 0x54, 0xAC, 0x13, 0x47, 0x9, 0x81, 0x91, 0xB2, 0x6C, 0xA9, 0xE6, 0x78, 0x12, 0xAB, 0xA0, 0x9C, 0xAA, 0xE6, 0x4, 0xDD, 0x97, 0x39, 0x9, 0x5, 0x69, 0xEC, 0xCD, 0x38, 0xD4, 0x31, 0x80, 0x2A, 0x34, 0xCC, 0x76, 0x23, 0x28, 0xA3, 0xB3, 0x97, 0x4E, 0x4F, 0x7, 0x9D, 0xF7, 0x89, 0x82, 0xBA, 0x32, 0x7E, 0x9B, 0x7B, 0x18, 0xE6, 0x86, 0xFA, 0x43, 0xCF, 0xEE, 0xDD, 0x35, 0xD3, 0x6B, 0xF, 0x10, 0xED, 0x54, 0x4, 0x4B, 0xC0, 0xD2, 0xE4, 0x2C, 0x6E, 0x34, 0xBA, 0xD4, 0xD2, 0xDB, 0xA7, 0x1E, 0x73, 0x4, 0xFA, 0xE6, 0xCD, 0xE7, 0x98, 0x26, 0xAE, 0x8C, 0xF1, 0x15, 0xF3, 0x4B, 0xEA, 0xF4, 0xC, 0xB6, 0xE6, 0x6E, 0xE2, 0xF4, 0xC5, 0x9, 0xB, 0x56, 0xD8, 0xB2, 0x4A, 0x42, 0x7A, 0xF6, 0xBF, 0x58, 0xB6, 0xD5, 0x27, 0xC5, 0xB9, 0x2, 0x8F, 0xAE, 0x9D, 0x75, 0x93, 0x2B, 0xCA, 0xD1, 0x28, 0x97, 0xC1, 0x8F, 0x0, 0x15, 0x35, 0xFA, 0x2E, 0x70, 0xFC, 0x90, 0x29, 0x9F, 0xA3, 0x6A, 0x16, 0x95, 0x29, 0x55, 0xD9, 0x2E, 0x58, 0xE0, 0x6A, 0x4F, 0xBF, 0x58, 0xB3, 0xB, 0xAA, 0xB4, 0x4C, 0xF6, 0xA3, 0xAD, 0x25, 0x37, 0x13, 0xDB, 0xCB, 0x95, 0x1E, 0x72, 0xF, 0x7, 0x3B, 0xB5, 0xF2, 0x1A, 0xF6, 0x9A, 0x66, 0x4, 0x7B, 0xC3, 0x4F, 0x6E, 0x5D, 0xB5, 0x56, 0xEF, 0x8B, 0x96, 0x6B, 0xD5, 0x80, 0xCC, 0x56, 0x55, 0x72, 0xA8, 0xEC, 0xB6, 0x85, 0xEB, 0x12, 0x2B, 0x36, 0xEA, 0xB1, 0xE4, 0xDD, 0xBB, 0x44, 0x61, 0x1A, 0xA1, 0x21, 0xE, 0x7D, 0x95, 0x73, 0xCB, 0x6A, 0x74, 0x89, 0x30, 0x62, 0xEA, 0x77, 0x70, 0x57, 0x8A, 0x8E, 0xD0, 0x5D, 0x33, 0xCD, 0xCE, 0xF9, 0x75, 0x3E, 0xDB, 0x37, 0x58, 0xA7, 0x44, 0x3B, 0x83, 0xF, 0x2B, 0x19, 0xF4, 0x11, 0xAC, 0x49, 0x57, 0xA8, 0x3, 0x40, 0xB, 0x84, 0x97, 0xB4, 0xD1, 0x17, 0xD, 0xB1, 0xFE, 0x12, 0xC, 0x47, 0x1E, 0x5F, 0xF9, 0x12, 0x79, 0x85, 0xAB, 0xDB, 0x63, 0xEF, 0xCE, 0x3D, 0xD5, 0x33, 0x8E, 0x2C, 0x35, 0xCE, 0x62, 0x25, 0x2E, 0xA6, 0xB5, 0x92, 0x49, 0x4F, 0x12, 0x8B, 0xF1, 0x8D, 0x83, 0xB8, 0x34, 0x7C, 0x9A, 0x77, 0x18, 0xE7, 0x84, 0xFE, 0x47, 0xCE, 0xEC, 0xDA, 0x36, 0xD0, 0x6F, 0x1F, 0x17, 0xEF, 0x51, 0x2, 0x4D, 0x7D, 0x6C, 0xF, 0xE5, 0x82, 0x8D, 0x16, 0xF, 0x66, 0x62, 0x5A, 0xD1, 0x9D, 0xB8, 0x47, 0x38, 0xC7, 0xE4, 0x9B, 0x23, 0xAF, 0x8E, 0xF8, 0x13, 0xF2, 0x49, 0xFE, 0xF2, 0xA, 0xB3, 0xE0, 0x6B, 0xE5, 0xF5, 0xD5, 0xD, 0xE, 0x51, 0xDA, 0xA0, 0x4C, 0x40, 0x7B, 0xF5, 0xBC, 0x5A, 0xB7, 0xD8, 0x27, 0xC4, 0xBB, 0x6, 0x8B, 0xAF, 0x9F, 0x72, 0x90, 0x28, 0xCE, 0xC1, 0x2F, 0x95, 0xC4, 0x89, 0x6, 0xA8, 0x8B, 0x11, 0xE7, 0x9C, 0x45, 0x3C, 0xF2, 0x2B, 0x1A, 0x97, 0xD9, 0x7B, 0x95, 0xE9, 0x7, 0x24, 0x5B, 0xE3, 0x6F, 0x4E, 0xBD, 0x50, 0xB5, 0xA, 0xA8, 0xA0, 0x4A, 0xF0, 0xA6, 0xAB, 0x20, 0x30, 0x13, 0xCE, 0xDF, 0x93, 0x1A, 0x73, 0xD, 0x1, 0x39, 0xB4, 0xFC, 0x1A, 0xF7, 0x98, 0x62, 0x0, 0x7A, 0xC1, 0x48, 0x6D, 0x5E, 0xB1, 0x46, 0xE8, 0x89, 0x93, 0x6D, 0xD3, 0x3D, 0x72, 0xBD, 0x9C, 0x9E, 0x11, 0x40, 0x6D, 0x31, 0x52, 0xEF, 0xE4, 0xD8, 0x56, 0xE, 0x3A, 0xD7, 0xB8, 0x47, 0x64, 0x1B, 0xA3, 0x2A, 0x8, 0x7C, 0x97, 0x67, 0xCD, 0x6C, 0x71, 0x8F, 0x35, 0x65, 0xEA, 0x62, 0x65, 0x51, 0x8E, 0x8F, 0xD2, 0x5B, 0x31, 0xCC, 0xC1, 0xF9, 0x74, 0x3C, 0xDF, 0x33, 0x59, 0xA5, 0x43, 0x38, 0x80, 0xB, 0x3B, 0x1E, 0xF6, 0x14, 0xAA, 0x4F, 0xEA, 0x16, 0xE8, 0x89, 0xE7, 0x3D, 0x3B, 0x6F, 0x65, 0xAE, 0xF0, 0x7E, 0x10, 0xAE, 0xB2, 0x99, 0x14, 0x5C, 0xFA, 0x17, 0x78, 0x87, 0xA1, 0xDD, 0x62, 0xED, 0xDA, 0x3B, 0xD3, 0x36, 0x88, 0x29, 0x32, 0xCE, 0x77, 0x37, 0x28, 0xA2, 0xB4, 0x90, 0x4F, 0x4D, 0x13, 0x9B, 0xF1, 0x8C, 0x81, 0xBC, 0x30, 0x7D, 0x98, 0x70, 0x1B, 0xE4, 0x80, 0xEE, 0x40, 0xCC, 0xE9, 0xDC, 0x30, 0x6D, 0xD1, 0xF4, 0xDE, 0x3, 0xE8, 0xAE, 0x96, 0xC9, 0xD5, 0xF2, 0x2A, 0x6C, 0x31, 0xAF, 0xD1, 0x6C, 0x61, 0x59, 0xD4, 0x9C, 0xBA, 0x52, 0x3E, 0xC6, 0xE6, 0x8F, 0x25, 0xA9, 0x8B, 0xFE, 0x16, 0xF5, 0x48, 0xEF, 0xF6, 0xF, 0xB4, 0xE2, 0x7D, 0xE3, 0xF7, 0xD3, 0xE, 0xD, 0x53, 0xDB, 0xB1, 0x4C, 0x41, 0x79, 0xF1, 0xB8, 0x5B, 0xB5, 0xDF, 0x24, 0xC7, 0xBF, 0x16, 0x8C, 0xAD, 0x9A, 0x74, 0x96, 0x95, 0x70, 0x2A, 0xE6, 0x79, 0x7D, 0x25, 0xDD, 0x1C, 0x32, 0xEC, 0x28, 0x72, 0xF9, 0x84, 0x2C, 0x21, 0x19, 0x94, 0xDC, 0x7A, 0x97, 0xFD, 0x1, 0x25, 0x59, 0xF7, 0x69, 0x48, 0xB8, 0x56, 0xB0, 0xD, 0xA8, 0xB5, 0x5A, 0xF6, 0xA2, 0xAA, 0x22, 0x36, 0x11, 0xCF, 0xCD, 0x93, 0x1B, 0x71, 0x9, 0x5, 0x38, 0xB6, 0xFB, 0x19, 0xF4, 0x9C, 0x72, 0x7, 0x78, 0xC4, 0x4E, 0x6B, 0xE3, 0xF, 0xAD, 0x21, 0x65, 0x2A, 0xC1, 0x8, 0x89, 0xCB, 0x40, 0x53, 0x70, 0xAD, 0xFB, 0xB3, 0x3B, 0x51, 0xEC, 0xE1, 0xD9, 0x54, 0x19, 0x3C, 0xD6, 0xBA, 0x53, 0x62, 0x1D, 0xA6, 0x2C, 0xD, 0x7B, 0x97, 0x72, 0xDC, 0x6A, 0x75, 0x8E, 0x37, 0x63, 0xE8, 0x63, 0x76, 0x51, 0x8F, 0x8D, 0xD6, 0x5F, 0x30, 0xCE, 0xC6, 0xFA, 0x77, 0x38, 0xCF, 0x34, 0x5B, 0xA0, 0x45, 0x3E, 0x3D, 0xB5, 0xD0, 0xD7, 0x1A, 0xAD, 0x6, 0x94, 0x5E, 0xAF, 0x15, 0x46, 0x9, 0x81, 0x81, 0xB1, 0x6F, 0xAD, 0xF3, 0x7B, 0x11, 0xAC, 0xA4, 0x9F, 0x15, 0x5E, 0xEE, 0x11, 0x7E, 0x82, 0xA7, 0xD8, 0x65, 0xED, 0xCF, 0x25, 0xD5, 0x32, 0x89, 0x2B, 0x34, 0xCC, 0x76, 0x23, 0x28, 0xA3, 0xB6, 0x94, 0x4B, 0x4C, 0x11, 0x9C, 0xF2, 0x8F, 0x85, 0xAC, 0x37, 0x7F, 0x9D, 0x76, 0x1D, 0x59, 0x3E, 0x5, 0x89, 0x20, 0x50, 0x70, 0xEB, 0xD9, 0x68, 0x9, 0x11, 0xED, 0x54, 0x1B, 0x48, 0xC3, 0xD6, 0xF1, 0x2F, 0x6D, 0x33, 0xBE, 0xD7, 0x6D, 0x63, 0x4D, 0xD2, 0x9A, 0xBF, 0x54, 0x3B, 0xC1, 0xE7, 0x9D, 0x21, 0xAC, 0x8C, 0xFC, 0xC, 0xF3, 0x4A, 0xE8, 0xF5, 0xC, 0xB6, 0xE3, 0x68, 0xE3, 0xF6, 0xD1, 0xA, 0x9, 0x52, 0xD9, 0xB6, 0x4F, 0x42, 0x7D, 0xE1, 0xBF, 0x59, 0xB0, 0xD9, 0x22, 0x7A, 0x1, 0xFD, 0x45, 0x41, 0x23, 0xD8, 0x4D, 0x21, 0xC9, 0xD7, 0x29, 0x97, 0xC1, 0x91, 0x3, 0x16, 0x31, 0xEF, 0x2D, 0x73, 0xFB, 0x94, 0x2A, 0x20, 0x1B, 0x80, 0xDA, 0x7C, 0x92, 0xFB, 0x4, 0x22, 0x59, 0xE2, 0x75, 0x4E, 0xBC, 0x57, 0xB2, 0xB, 0xAA, 0xB4, 0x4C, 0xF6, 0xA3, 0xA8, 0x26, 0x32, 0x10, 0xCD, 0xCA, 0x90, 0x18, 0x75, 0x19, 0x2, 0x3A, 0xB3, 0xFD, 0x1F, 0x49, 0x22, 0x99, 0xCE, 0x94, 0x7D, 0xE2, 0xB0, 0x57, 0xB6, 0x50, 0xEE, 0x8B, 0x96, 0x76, 0xD6, 0x83, 0xC8, 0x43, 0x56, 0x71, 0xAF, 0xE8, 0xB5, 0x3A, 0x53, 0xF8, 0xE7, 0xDF, 0x51, 0x1F, 0x39, 0xD1, 0xBA, 0x46, 0x7F, 0x1B, 0xA2, 0x2D, 0xF, 0x7D, 0x95, 0x73, 0xCB, 0x6A, 0x74, 0x8C, 0x33, 0x67, 0xE9, 0x61, 0x71, 0x52, 0x8C, 0x89, 0xC6, 0x58, 0x32, 0xCB, 0xC0, 0xFC, 0xCA, 0x86, 0x24, 0xFD, 0xB7, 0x19, 0xE9, 0xE5, 0x89, 0xC, 0x2D, 0x18, 0xF4, 0x11, 0xB0, 0x4A, 0x54, 0xAC, 0x16, 0x43, 0x8, 0x83, 0x93, 0xB7, 0x6E, 0xAF, 0xE7, 0x7D, 0x17, 0xA9, 0xA2, 0x9A, 0x12, 0x5E, 0xFB, 0xB, 0x78, 0x86, 0xA6, 0xDA, 0x63, 0xEF, 0xCE, 0x3D, 0xD5, 0x33, 0x8B, 0x2F, 0x30, 0xCD, 0x74, 0x24, 0x2B, 0xA0, 0xB2, 0x84, 0x4C, 0x4E, 0x14, 0x9A, 0xF4, 0x32, 0x3B, 0x47, 0xFE, 0x93, 0x24, 0xDA, 0xC6, 0xED, 0x87, 0xF8, 0x46, 0xCE, 0xEC, 0xC1, 0x35, 0xD3, 0x6B, 0xA, 0x14, 0xEC, 0x56, 0x6, 0x4E, 0xC2, 0xD4, 0xE5, 0x29, 0x6B, 0x36, 0xB8, 0xD2, 0x6A, 0x62, 0x5E, 0xD6, 0x9F, 0xB8, 0x56, 0x25, 0xC7, 0xE5, 0x99, 0x22, 0xAF, 0x8E, 0xFD, 0x15, 0xF3, 0x4B, 0xEA, 0xF1, 0x8, 0xB7, 0xE1, 0x6F, 0xE0, 0xF5, 0xD5, 0x1A, 0xE, 0x50, 0xDC, 0xB0, 0x49, 0xFF, 0xC3, 0xA, 0x76, 0xB5, 0x9, 0x75, 0xF9, 0xCE, 0xB8, 0x0, 0x8A, 0xAF, 0x9F, 0x68, 0x93, 0x2B, 0xCA, 0xD4, 0x2C, 0x96, 0xC3, 0x8D, 0x5, 0x17, 0x33, 0xFB, 0x2B, 0x75, 0xFE, 0x92, 0x2F, 0x27, 0x1B, 0x95, 0xC2, 0x7A, 0x96, 0xFA, 0x6, 0x24, 0x5B, 0xE3, 0x6F, 0x4E, 0xBD, 0x55, 0xB6, 0xF, 0xAB, 0xB6, 0x4B, 0xF5, 0xA0, 0xAC, 0x36, 0x35, 0x12, 0xC8, 0xCC, 0x96, 0xA5, 0xCB, 0xF2, 0xCB, 0xD6, 0xA, 0x51, 0xC4, 0xFD, 0x9B, 0x64, 0x1, 0x7A, 0xC1, 0x51, 0x6E, 0x5D, 0xB5, 0x53, 0xEB, 0x8A, 0x94, 0x69, 0xD0, 0x82, 0xCA, 0x57, 0x50, 0x77, 0xAA, 0xEE, 0xB0, 0x3D, 0x53, 0xED, 0xFE, 0xD9, 0x55, 0x1E, 0x3B, 0xD7, 0xB8, 0x47, 0x64, 0x1B, 0xA3, 0x2F, 0xB, 0x79, 0x94, 0x71, 0xCC, 0x69, 0x77, 0x88, 0x23, 0x60, 0xEB, 0x64, 0x77, 0x54, 0x31, 0x37, 0x2D, 0x91, 0xDE, 0x72, 0x6C, 0x27, 0x7E, 0x3F, 0xD9, 0x32, 0x59, 0xA5, 0x5B, 0x3B, 0x83, 0xF, 0x2E, 0x1D, 0xF5, 0x13, 0xAE, 0x4C, 0x55, 0xAE, 0x2, 0x45, 0xE, 0x86, 0x95, 0xB2, 0x69, 0xAC, 0xF4, 0x16, 0xF7, 0x40, 0x7F, 0x9C, 0x14, 0x5C, 0xFA, 0x10, 0x7B, 0x84, 0xA3, 0xDA, 0x6B, 0xE4, 0xCE, 0x3D, 0xD5, 0x33, 0x8B, 0x2A, 0x34, 0xC9, 0x75, 0x20, 0x20, 0xAC, 0xBF, 0x92, 0x57, 0x4E, 0x1B, 0x99, 0xF8, 0x8D, 0x86, 0xD4, 0xD2, 0x90, 0x44, 0x72, 0x18, 0xE7, 0x84, 0xFC, 0x40, 0xCC, 0xE9, 0xDC, 0x3D, 0xD8, 0x6B, 0xA, 0x14, 0xEC, 0x56, 0x3, 0x48, 0xC6, 0xD5, 0xF2, 0x27, 0x62, 0x3A, 0xB8, 0xC9, 0x6F, 0x68, 0x5B, 0xDD, 0x9D, 0xBD, 0x3A, 0xDE, 0x2B, 0x3A, 0x9E, 0x23, 0xAF, 0x8E, 0xFA, 0x16, 0xF0, 0x4C, 0xEB, 0xFC, 0x7, 0xB6, 0xE3, 0x68, 0xE3, 0xF6, 0xD1, 0xF, 0x8, 0x50, 0xD8, 0xB9, 0x43, 0x48, 0x7A, 0xEC, 0xBF, 0x50, 0xB5, 0xD1, 0x26, 0xC3, 0xD6, 0xE5, 0x63, 0x70, 0x98, 0x75, 0x93, 0x2B, 0xCD, 0xD7, 0x2F, 0x91, 0xC2, 0x80, 0x8, 0x16, 0x31, 0xEF, 0x2D, 0x73, 0xFB, 0x91, 0x29, 0x22, 0x1A, 0x9C, 0xD3, 0x73, 0x94, 0xE0, 0x4, 0x2F, 0x59, 0xEA, 0x6E, 0x49, 0xD0, 0xB3, 0x5F, 0xD5, 0xAF, 0xB4, 0x4C, 0xF6, 0xA4, 0xAB, 0x20, 0x31, 0x10, 0xC7, 0xC6, 0x93, 0x1B, 0x71, 0xC, 0x1, 0x39, 0xB4, 0xF9, 0x19, 0xF4, 0x90, 0x68, 0xD, 0x78, 0xDB, 0x4C, 0x62, 0x5F, 0xBC, 0x52, 0xEC, 0xE7, 0x72, 0x80, 0x8, 0x86, 0xC8, 0x43, 0x56, 0x76, 0xAC, 0xEE, 0xB4, 0x3A, 0x59, 0xE7, 0xE1, 0xD9, 0x54, 0x1C, 0x3A, 0xD7, 0xB8, 0x42, 0x67, 0x18, 0xAB, 0x20, 0x7, 0x7E, 0x8D, 0x70, 0xC6, 0x68, 0x7D, 0x8D, 0x31, 0xE, 0xE, 0x8F, 0xA8, 0x54, 0x8F, 0x8D, 0xD3, 0x5C, 0x32, 0xCF, 0xC6, 0xF8, 0x7C, 0x37, 0xDA, 0x37, 0x58, 0xA7, 0x44, 0x3B, 0x83, 0xA, 0x2D, 0x1E, 0xFD, 0x1C, 0xA2, 0x49, 0x4C, 0xAF, 0x18, 0x41, 0x1, 0x82, 0x91, 0xDC, 0x89, 0x41, 0x2D, 0x7E, 0x11, 0xAC, 0xA1, 0x9E, 0x17, 0x5F, 0xFD, 0x16, 0x70, 0x8C, 0xA4, 0xDB, 0x63, 0xEF, 0xCE, 0x3D, 0xD5, 0x36, 0x88, 0x29, 0x3C, 0xC3, 0x7F, 0x20, 0x30, 0xA0, 0xB9, 0x93, 0x46, 0x4C, 0x19, 0x9B, 0xF1, 0x8C, 0x81, 0xB9, 0x34, 0x7C, 0x9A, 0x76, 0x13, 0xF7, 0x84, 0xFB, 0x43, 0xCF, 0xEE, 0xDD, 0x35, 0xD2, 0x64, 0xA, 0x16, 0xEC, 0x56, 0x3, 0x48, 0xC3, 0xD6, 0xF4, 0x20, 0x62, 0x39, 0xAC, 0xDD, 0x63, 0x60, 0x54, 0xC4, 0x9E, 0xBA, 0x57, 0x38, 0xC7, 0xE4, 0x9B, 0x26, 0xA2, 0x83, 0xF7, 0x2, 0xFD, 0x46, 0xFA, 0xF8, 0x2, 0xA5, 0xA5, 0x61, 0xE2, 0xF9, 0xD0, 0xF, 0xD, 0x53, 0xDB, 0xB1, 0x4C, 0x41, 0x7C, 0xFE, 0xB6, 0x55, 0xA7, 0xD2, 0x2C, 0xD7, 0x45, 0xB, 0x8E, 0xAE, 0x9C, 0x75, 0x93, 0x2B, 0xCA, 0xD4, 0x2C, 0x96, 0x3C, 0x89, 0x3, 0x16, 0x31, 0xEF, 0x2D, 0x73, 0xFB, 0x91, 0x2C, 0xDE]
opcode = decrypt(opcode)
enc = [0xB6, 0x82, 0x1A, 0x15, 0xF5, 0x32, 0x5A, 0xFC, 0xF, 0x11, 0xEA, 0x89, 0x32, 0x38, 0xC3, 0x55]
enc = decrypt(enc)
_rand_array = [0x9B, 0x71, 0x29, 0x14, 0xD4, 0x35, 0x39, 0x64, 0x3D, 0x95, 0x9A, 0x93, 0xF6, 0xC7, 0x22, 0x58, 0xD0, 0xB4, 0xEE, 0x4F, 0x88, 0x2D, 0x4, 0x51, 0x6A, 0xE7, 0xA9, 0x7, 0x24, 0x3F, 0x46, 0xF1, 0xA1, 0x3A, 0x1F, 0x5F, 0xCA, 0x12, 0xE2, 0x24, 0xD6, 0xB7, 0xA6, 0x25, 0x69, 0xE3, 0x40, 0xA5, 0x5A, 0x49, 0xA8, 0x92, 0xF1, 0xCF, 0x20, 0x73, 0x1A, 0x81, 0xB4, 0xEA, 0x29, 0x9B, 0x56, 0xAB, 0x9F, 0x92, 0x1, 0x28, 0xC0, 0xEA, 0x63, 0x99, 0x83, 0x12, 0x18, 0x8B, 0x59, 0x9D, 0x35, 0xEC, 0xAD, 0x5C, 0x6D, 0x2E, 0x86, 0x57, 0x9D, 0x68, 0xF9, 0x94, 0x3C, 0xA, 0xF0, 0x42, 0x3F, 0x84, 0x1F, 0xB6, 0xF4, 0x5, 0x1F, 0x99, 0x3, 0xBF, 0xF0, 0x25, 0xE2, 0xEC, 0xAB, 0xA4, 0x5C, 0xAC, 0x52, 0xAC, 0x14, 0x86, 0xBC, 0x17, 0xE8, 0xFB, 0x79, 0xE9, 0x87, 0x10, 0x25, 0x0, 0x2F, 0xFD, 0x5C, 0x7F, 0x1E, 0xD1, 0x87, 0xC5, 0x97, 0x5D, 0x5C, 0xA7, 0x2, 0xAA, 0x42, 0xD4, 0xCA, 0x27, 0x91, 0xE0, 0x50, 0xB6, 0x1C, 0x4, 0x1E, 0x42, 0x4B, 0xE8, 0x54, 0x6A, 0xF0, 0xCB, 0xD1, 0xFB, 0xA1, 0x34, 0x9A, 0xCE, 0xCB, 0xCD, 0xB, 0x4A, 0x2D, 0x98, 0xA8, 0xBB, 0x3A, 0x65, 0x14, 0xE7, 0x4B, 0xD5, 0x1D, 0x2F, 0xBF, 0x22, 0x1E, 0x61, 0x76, 0x2F, 0x8D, 0x30, 0xB0, 0x6C, 0x99, 0xCA, 0x9F, 0x5C, 0x5D, 0xC8, 0xE9, 0xBC, 0xF0, 0xA9, 0x94, 0x57, 0x62, 0xF, 0x22, 0x21, 0x1E, 0x3B, 0xD7, 0xEE, 0x24, 0x5E, 0xC9, 0xFF, 0x8C, 0x4C, 0x75, 0x1E, 0xF0, 0x4, 0xB2, 0x38, 0xC, 0x20, 0xC6, 0x8C, 0x1F, 0x33, 0x6, 0x38, 0xFF, 0x2F, 0x1D, 0xAB, 0x45, 0xF3, 0x35, 0x92, 0xE2, 0xBD, 0xD7, 0x69, 0x28, 0x4A, 0xDE, 0x19, 0xDB, 0x8A, 0x4F, 0x6E, 0xB5, 0xF4, 0xED, 0xBD, 0xC, 0x1B]
rand_array = z3.Array('rand_array', z3.BitVecSort(64),z3.BitVecSort(8))
flag = z3.BitVecs(" ".join(f"idx{i}" for i in range(32)),8)
for i in range(len(_rand_array)): rand_array = z3.Store(rand_array,i,_rand_array[i])
stack = [0]*0x20
buffer = [0]*0x400
for i in range(len(flag)): buffer[i] = flag[i]
for i in range(len(enc)): buffer[0x210+i] = enc[i]
PC = 0
ZF,CF = False,False
solver = z3.Solver()
while PC < len(opcode):
mask = (1<<64)-1
match opcode[PC]:
case 0x00:
break
case 0x01:
op0,op1 = opcode[PC+1]&0x0F,unpack("<Q",opcode[PC+2:PC+2+8])[0]
stack[op0] = op1
PC += 10
case 0x02:
op0,op1 = opcode[PC+1]&0x0F,unpack("<H",opcode[PC+2:PC+2+2])[0]
stack[op0] = z3.ZeroExt(56,buffer[op1])
PC += 4
case 0x03:
op0,op1 = unpack("<H",opcode[PC+1:PC+1+2])[0],opcode[PC+3]&0x0F
buffer[op0] = z3.Extract(7,0,stack[op1])
PC += 4
case 0x05:
op0,op1,op2 = opcode[PC+1]&0x0F,opcode[PC+2]&0x0F,opcode[PC+3]&0x0F
num1,num2 = stack[op1],stack[op2]
num0 = (num1+num2)&mask
stack[op0] = num0
PC += 4
case 0x07:
op0,op1,op2 = opcode[PC+1]&0x0F,opcode[PC+2]&0x0F,opcode[PC+3]&0x0F
num1,num2 = stack[op1],stack[op2]
num0 = (num1*num2)&mask
stack[op0] = num0
PC += 4
case 0x0A:
op0,op1,op2 = opcode[PC+1]&0x0F,opcode[PC+2]&0x0F,opcode[PC+3]&0x0F
num1,num2 = stack[op1],stack[op2]
num0 = (num1^num2)&mask
stack[op0] = num0
PC += 4
case 0x0F:
op0,op1,op2 = opcode[PC+1]&0x0F,opcode[PC+2]&0x0F,opcode[PC+3]
num1 = stack[op1]
num0 = (num1 >> op2)&mask
stack[op0] = num0
PC += 4
case 0x10:
op0,op1 = opcode[PC+1]&0x0F,opcode[PC+2]&0x0F
num1,num2 = stack[op0],stack[op1]
ZF = num1 == num2
CF = num1 < num2
PC += 3
case 0x13:
op0 = unpack("<H",opcode[PC+1:PC+1+2])[0]
if PC == 0x0923:
solver.add(ZF == True)
PC += 3
continue
if ZF: PC += 3
else :PC = op0
if PC > len(opcode):break
case 0x14:
op0,op1 = opcode[PC+1]&0x0F,opcode[PC+2]&0x0F
num1 = stack[op1]
num0 = rand_array[num1]
stack[op0] = z3.ZeroExt(56,num0)
PC += 3
case 0x15:
rol = lambda num,bits:((num<<bits) | (num>>(64-bits)))&mask
op0,op1,op2 = opcode[PC+1]&0x0F,opcode[PC+2]&0x0F,opcode[PC+3]
num1 = stack[op1]
num0 = rol(num1,op2)
stack[op0] = num0
PC += 4
case 0x17:
op0,op1 = opcode[PC+1]&0x0F,opcode[PC+2]&0x0F
num1 = stack[op1]
num0 = buffer[num1]
if isinstance(num0,z3.BitVecRef):num0 = z3.ZeroExt(56,num0)
stack[op0] = num0
PC += 3
case 0xFF:
break
case default:
raise NotImplementedError(f"Unkonwn opcode 0x{default:02X}")
result = solver.check()
result = solver.model()
print([result[i] for i in flag])
|